Learn SCADA by attending SCADA Training Course at TONEX
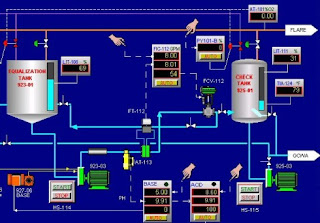
SCADA (Supervisory Control And Data Acquisition) systems also known as Industrial Control System (ICS) run mission critical infrastructure such as telecom, nuclear plants, manufacturing, oil and gas refining plants, wind and solar power generation, gas pipelines, power grid, water treatment, chemical manufacturing, airports, and transportation.The following is a list of the major control components of SCADA:
- Control Server. The control server hosts the DCS or PLC supervisory control software that is designed to communicate with lower-level control devices. The control server accesses subordinate control modules over an ICS network.
- SCADA Server or Master Terminal Unit (MTU) or Master Station. The SCADA Server is the device that acts as the master in a SCADA system. Remote terminal units and PLC devices (as described below) located at remote field sites usually act as slaves.
With SCADA systems, master station receives inputs from remote terminal units (RTU) that are connected to field instrumentation such as process ovens. When polled by the SCADA master, the RTUs transmit data to the central host for processing. SCADA software then logs alarms and displays the data graphically.
Our SCADA instructors have SCADA, SCADA security, Network Security and IT security expertise, a unique combination.